So today I needed to deploy a System Center Operations Manager Gateway in our perimeter network to support external client connections from third party locations and environments that are not part of our internal corp domain. I thought I would write up the vast majority of my steps for future reference and hopefully to help you. I used primarily two sources of information in additional to my general knowledge, both are listed at the bottom of this post.
1. Deploy Windows Server 2012 R2 standalone Server
2. Install Updates
3. Rename the server
4. Host File:
It is very important that all servers are able to resolve the FQDN of each other. Typically this is done through DNS, but if DNS is not possible you should have all the servers setup in a host file.
a. On all of the Management group servers that are unable to use DNS to resolve the FQDN of the Gateway Server edit the host file found locally in “C:\Windows\System32\drivers\etc”
b. Open file with Notepad as a admin with elevated rights
c. Enter the IP address and FQDN of the Gateway servers
d. On all of the Gateway servers enter all the Management group servers that the gateway will connect to
On the Management Server you should have something like:
192.168.0.100 managementserver1.domain1.com
192.168.0.101 managementserver2.domain1.com
On the Gateway Server you should have
99.100.99.100 gatewayserver1.domain2.com
99.100.99.101 gatewayserver2.domain2.com
Save the file and close Notepad.
5. Firewall:
Before you begin you need to make sure that if there are any firewalls between the servers that port 5723 is open.
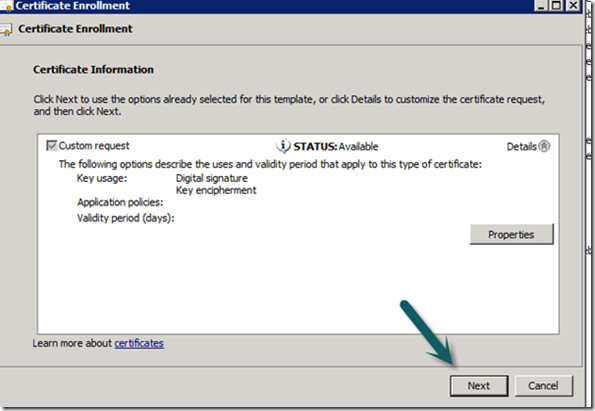
6. Certificates:
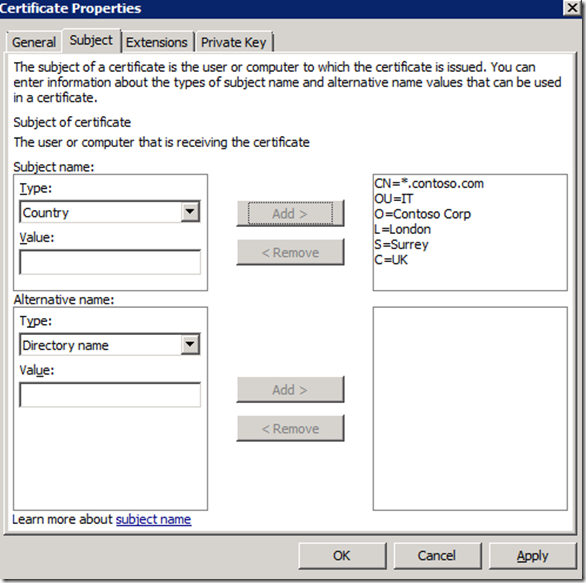
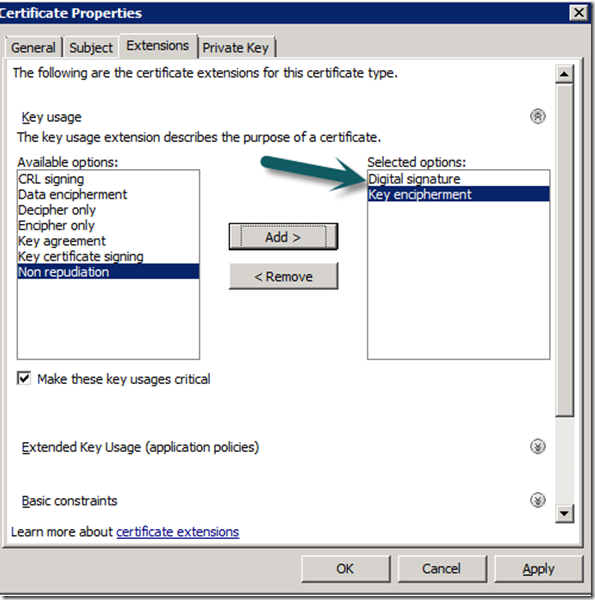
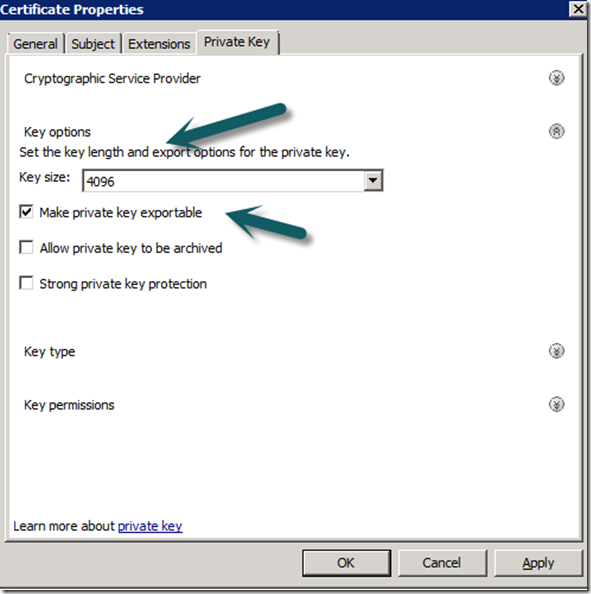
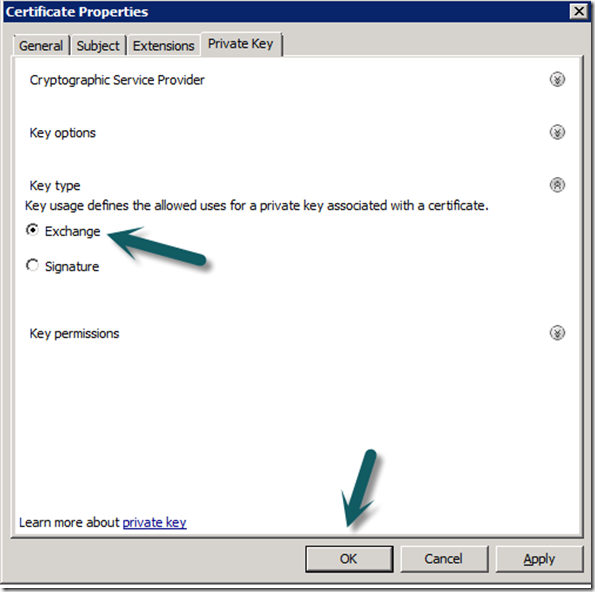
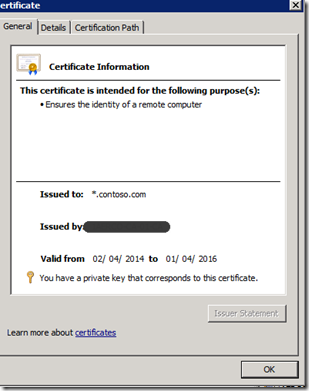
Deploying gateway servers requires certificates on all servers in the management group and all gateway servers. These can be internal via a CA or external from a third party vendor like VeriSign. I use an internal CA which is already setup to issue SCOM Gateway Certificates, you can find more information on how to set this up from the sources link at the bottom.
7. Ensure The Management Servers has an Ops Manager Certificate install in it Personal Computer Store, if you do not have one, enrol.
8. Gateway Root Certificate Import
On the Gateway Server, install the CA root certificate.
a. Browse to https://<CA Issuing Server>/certsrv
b. Authenticate
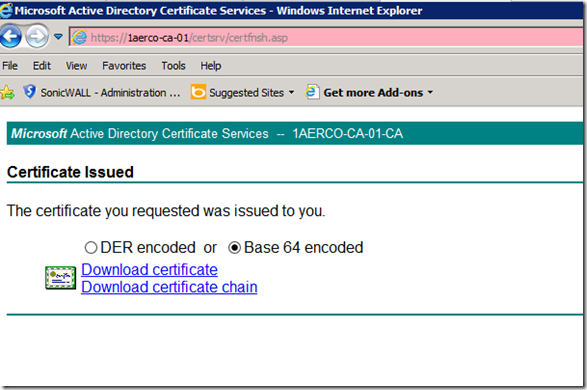
c. Select the “Download a CA certificate, certificate chain, or CRL link on the web page.
d. Select “Base 64” as the encoding method
e. Select “Download CA certificate chain” and save the file.
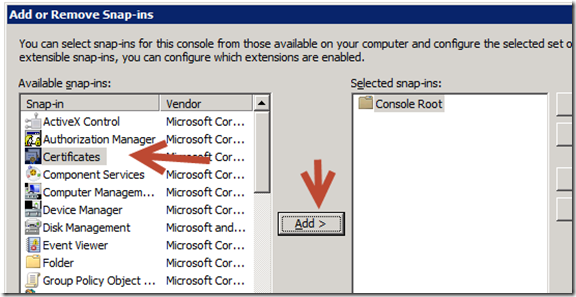
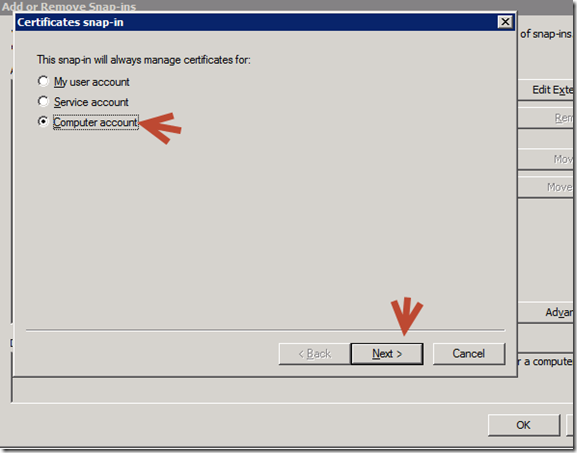
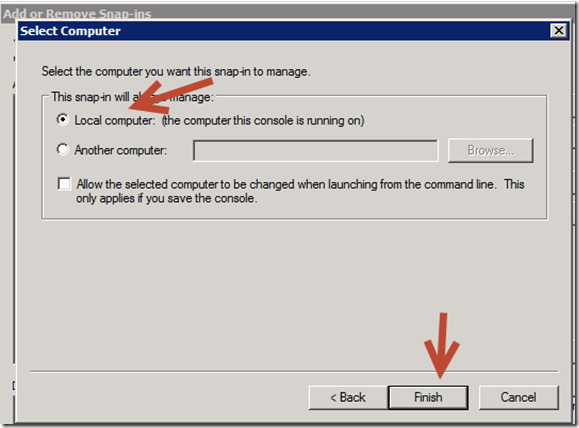
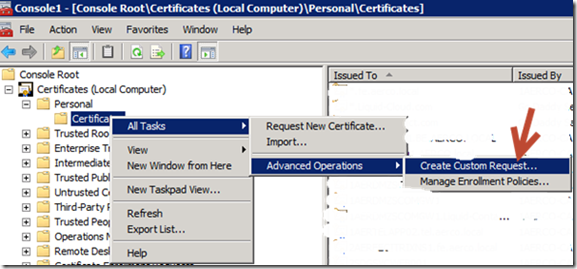
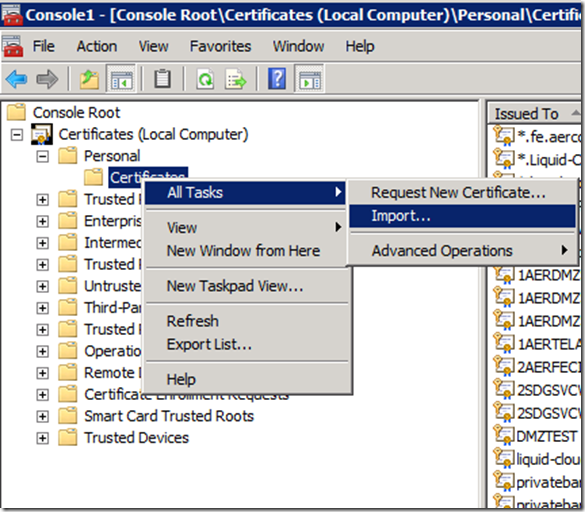
f. Open MMC and add the certificate snapin for the local computer.
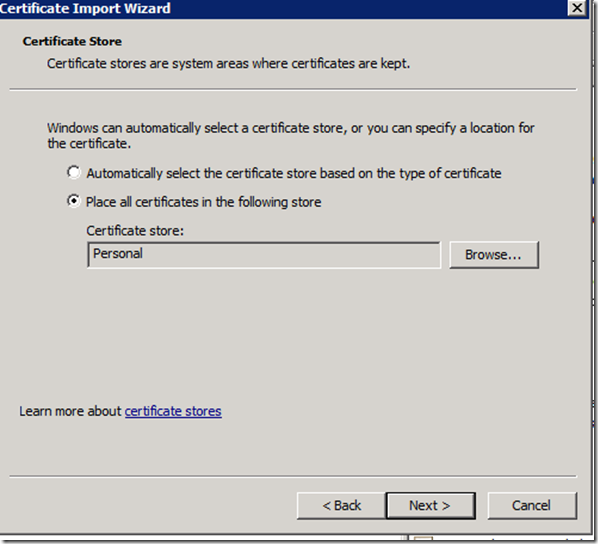
g. Right click the Trusted Root Certification Authorities\Certificates store and select All Tasks\Import, import the downloaded file into the store. This will ensure that any certificate issued by the internal CA will be trusted by this machine.
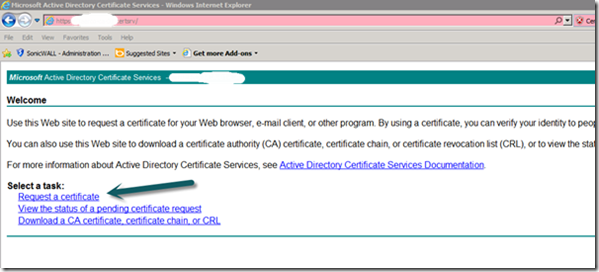
9. Gateway Server SCOM Certificate
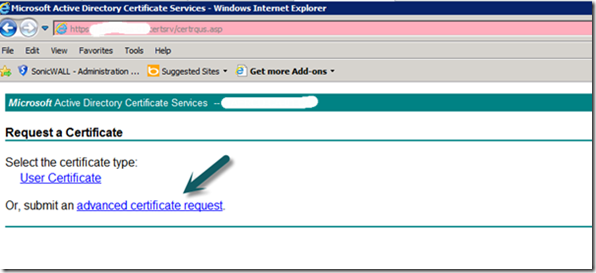
a. From the Gateway server browse to https://<CA Issuing Server>/certsrv
b. Select “Request a Certificate”
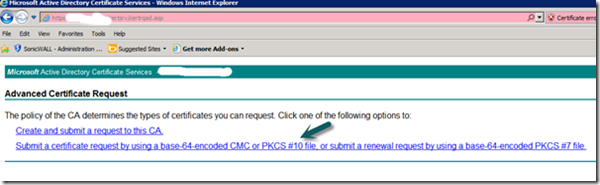
c. Select “Advanced Certificate Request”
d. Select “Create and Submit a request to this CA” If you do not get a prompt check your ActiveX settings as you should get a prompt.
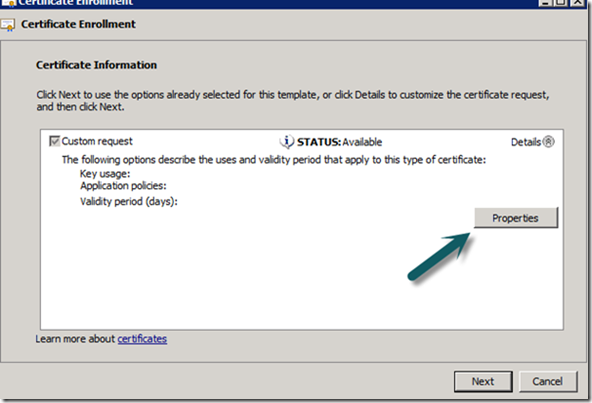
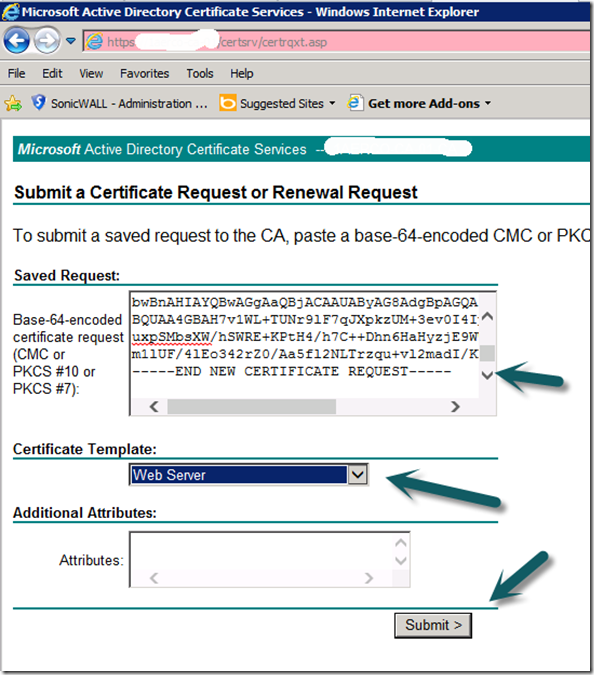
e. Select your Operations Manager certificate form the “Certificate Template” option (Drop Down).
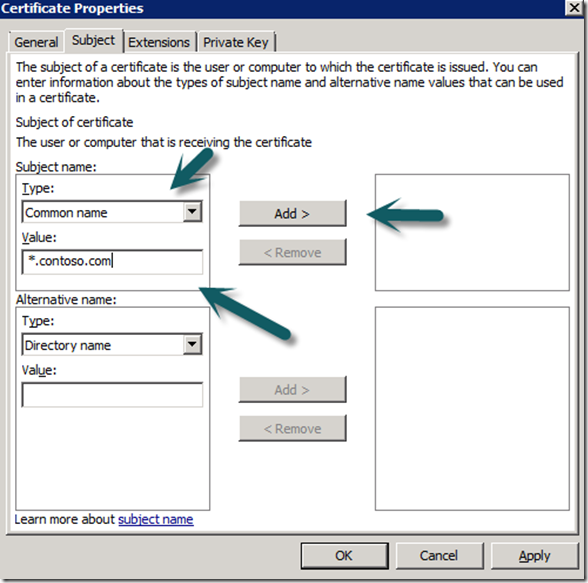
f. In the name field populate with the FQDN of the Gateway Server in the server is in a domain, if it is in a workgroup use the server name..
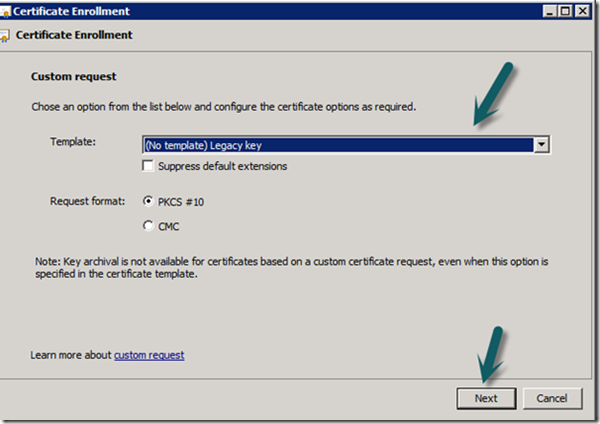
g. Select PKCS10 as the request format
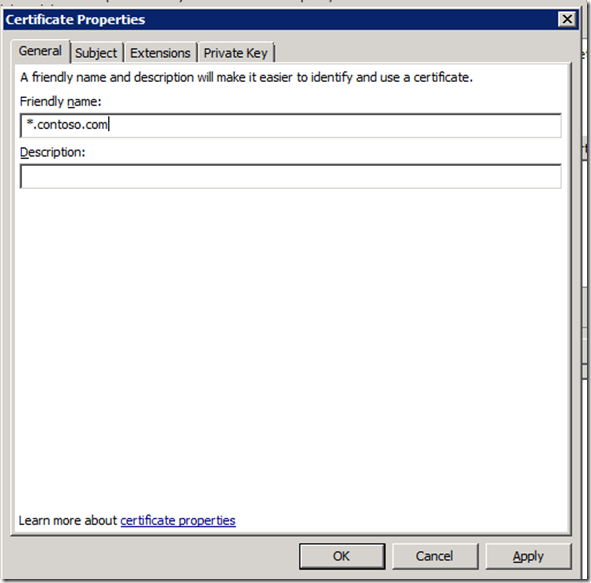
h. Provide a friendly name so you can identify the certificate at a later date.
i. Select “Submit”
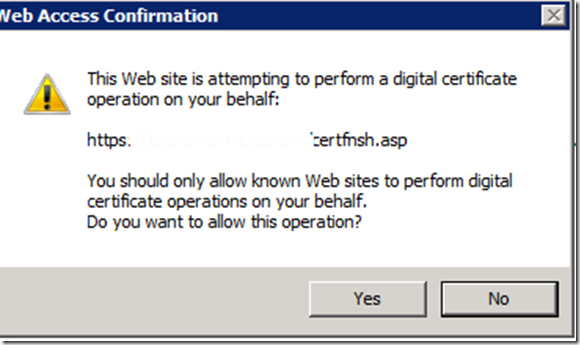
j. Select yes to any popups
k. Select “Install this certificate”
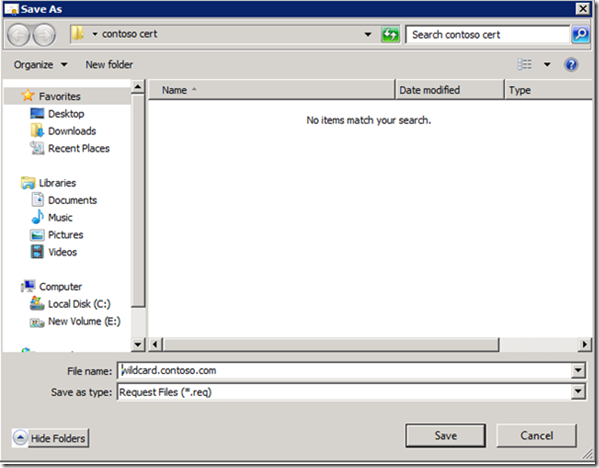
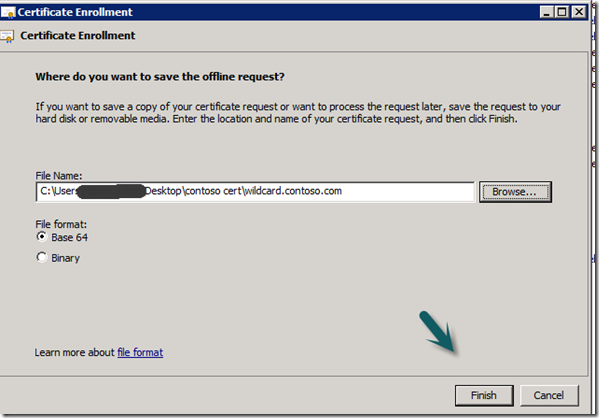
10. Move the Certificate to the correct location
a. On the gateway server in the Certificate MMC for the user export the new certificate to file exporting the private key and import into the personal certificate store for the local computer.
b. Restart the health service (Microsoft Monitoring Agent)
11. Gateway Approval Tool
Now that we have our certs in place we need to run the gateway approval tool on the SCOM RMS server. In the installation media in SUPPORTTOOLS under your respective processor folder you will find two files:
Microsoft.EnterpriseManagement.GatewayApprovalTool.exe
Microsoft.EnterpriseManagement.GatewayApprovalTool.exe.config
a. Copy both of these files to the SCOM install directory under <installed Drive>Program Files\System Center 2012 R2\Operations Manager\Setup and run the following command in that folder from an elevated command prompt.
Microsoft.EnterpriseManagement.gatewayApprovalTool.exe /ManagementServerName=<FQDN of RMS box> /GatewayName=<FQDN of Gateway Server> /Action=Create
Note: If you are installing a Gateway server in a domain then use the FQDN of the gateway server, if you are installing the gateway in a workgroup just using the server name.
Once complete the command prompt should say something like “The approval of the server <gateway server FQDN> completed successfully”
12. Install Gateway Role
Now we have everything in place to deploy the gateway role.
a. Using the Operation Manager Install media install the “Gateway Management Server” Role using the link on the install media splash screen.
b. Once installed, go back to the SCOM console, in Administration view under Management servers select the properties of the new gateway server and in the security tab enable the server proxy.
c. On the gateway server we need to tell SCOM which certificate to use for authentication, by running the MOMCERTIMPORT.exe tool. In the installation media in SUPPORTTOOLS under your respective processor folder run the MOMCERTIMPORT.exe tool from an elevated command prompt. You should see the cert that you installed previously. Select the correct certificate and Click OK
Sources:
http://jimmoldenhauer.blogspot.co.uk/2012/11/scom-2012-install-and-configure-gateway.html
http://technet.microsoft.com/en-us/library/hh456445.aspx